利用Graylog接入F5的RequestLog请求日志并结合F5的iRules拦截攻击IP
利用Graylog接入F5的RequestLog请求日志并结合F5的iRules拦截攻击IP

yuanfan2012
发布于 2025-11-18 12:33:27
发布于 2025-11-18 12:33:27

本文参考如下链接完成
1. https://my.f5.com/manage/s/article/K00847516
2. https://my.f5.com/manage/s/article/K73554344
3. https://techdocs.f5.com/kb/en-us/products/big-ip_ltm/manuals/product/bigip-external-monitoring-implementations-13-0-0/2.html
4. https://www.cnblogs.com/JetpropelledSnake/p/10564448.html
5. https://www.cnblogs.com/JetpropelledSnake/p/10550778.html
一、F5侧配置
1、先配置pool,将graylog服务器IP+syslog input端口作为pool成员
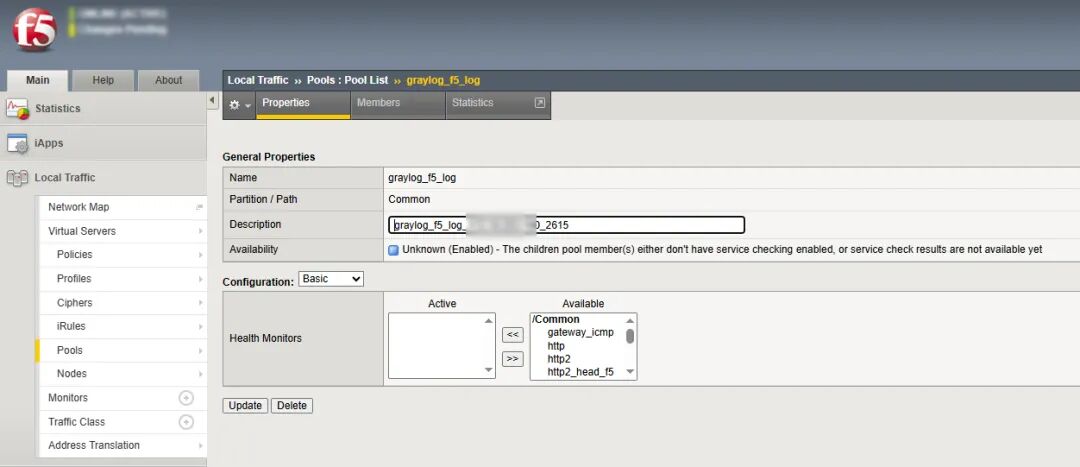
(图片点击放大查看)

(图片点击放大查看)
2、创建Request Logging的Profiles
例如vs_logging_to_graylog
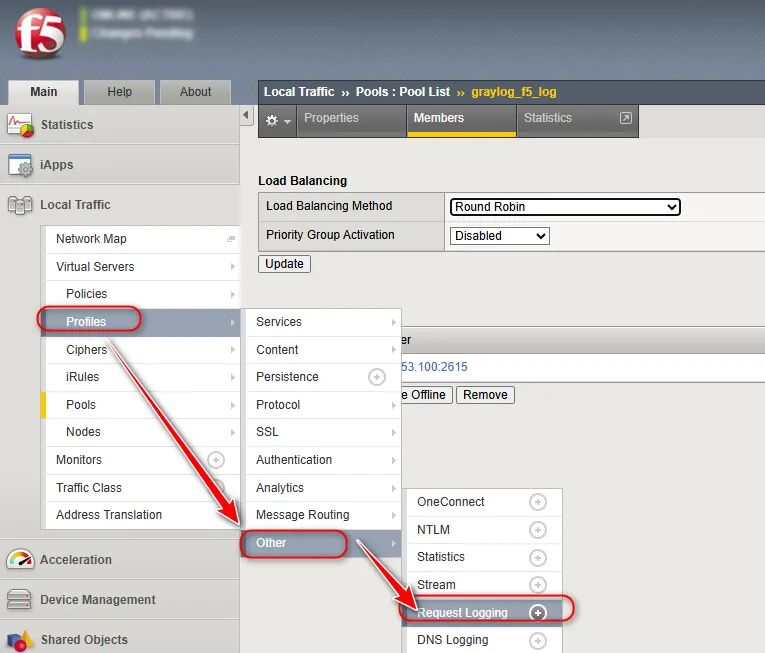
(图片点击放大查看)
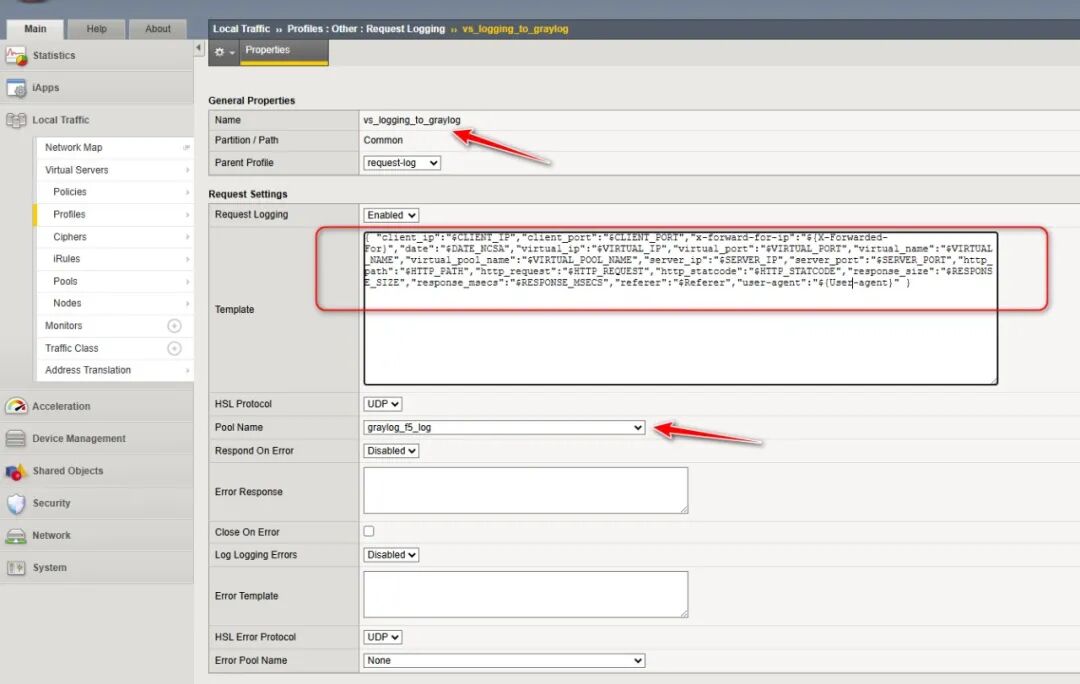
(图片点击放大查看)
模板内容为
{ "client_ip":"{X-Forwarded-For}","date":"VIRTUAL_IP","virtual_port":"VIRTUAL_NAME","virtual_pool_name":"SERVER_IP","server_port":"HTTP_PATH","http_request":"HTTP_STATCODE","response_size":"RESPONSE_MSECS","referer":"
上面的这个变量参考Request logging parameters变量表,添加你需要的参数
我这边构造成json格式,方便Graylog进行JSON日志解析
3、接下来在VS中应用这个vs_logging_to_graylog 的Request Logging Profile
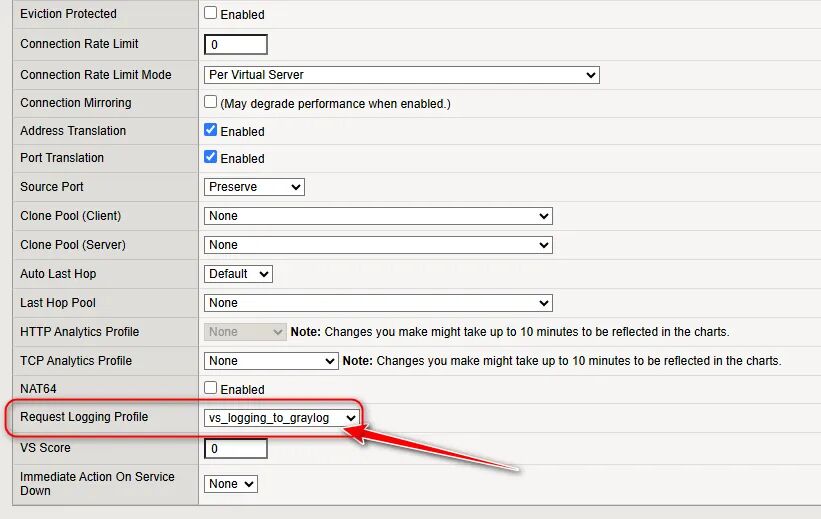
(图片点击放大查看)
二、GrayLog侧配置
1、添加一个syslog 的input,端口与F5中配置的pool成员中一致
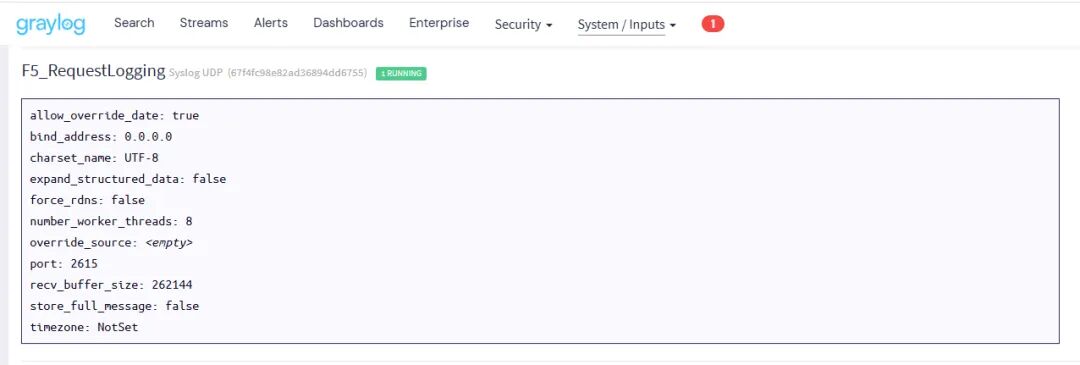
(图片点击放大查看)
2、针对采集的日志配置一下Json提取器
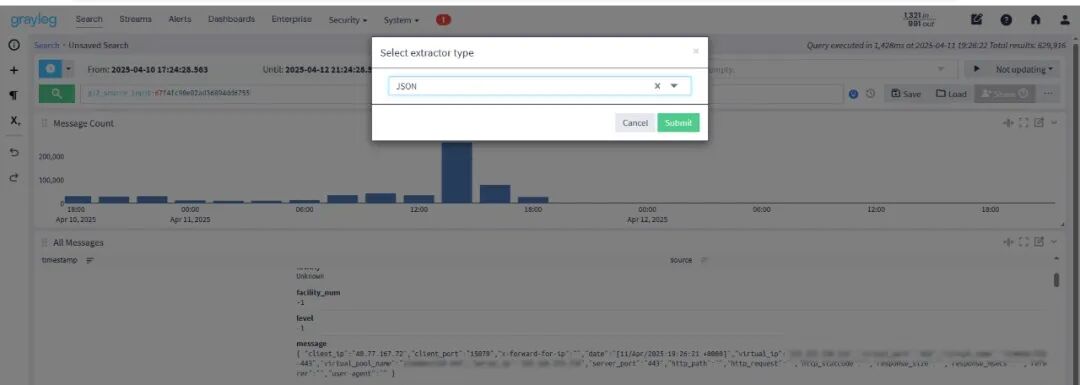
(图片点击放大查看)
3、Graylog上最终访问VS的日志效果如下
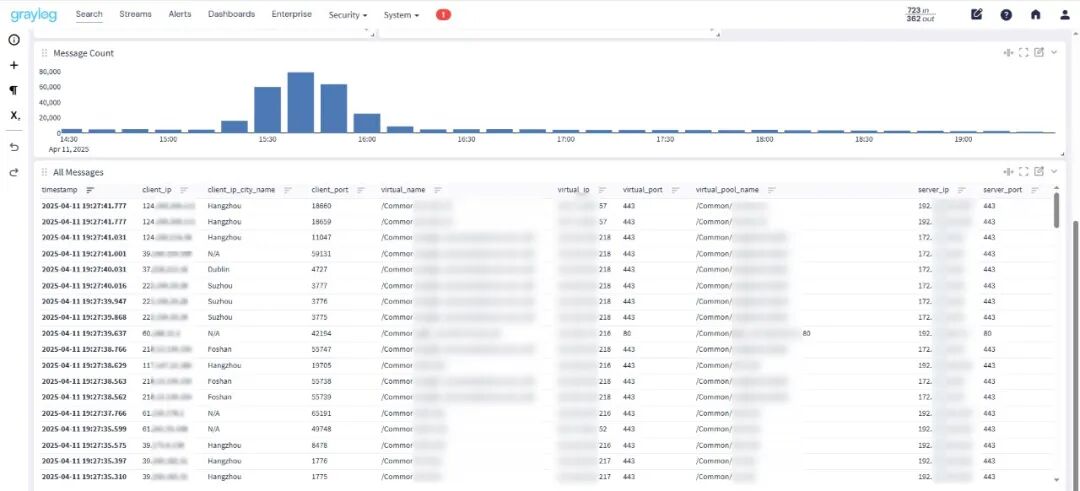
(图片点击放大查看)
三、结合F5的iRules拦截攻击IP
针对访问IP的访问日志,可以结合安全威胁情报(例如微步)或者内部态势感知等等安全告警 判断是否封锁攻击IP 可以联动防火墙进行封锁
可以结合F5的iRules拦截攻击IP
步骤如下
1、新建 iRules中的Data Group List
例如BlockListIP_DataGroup
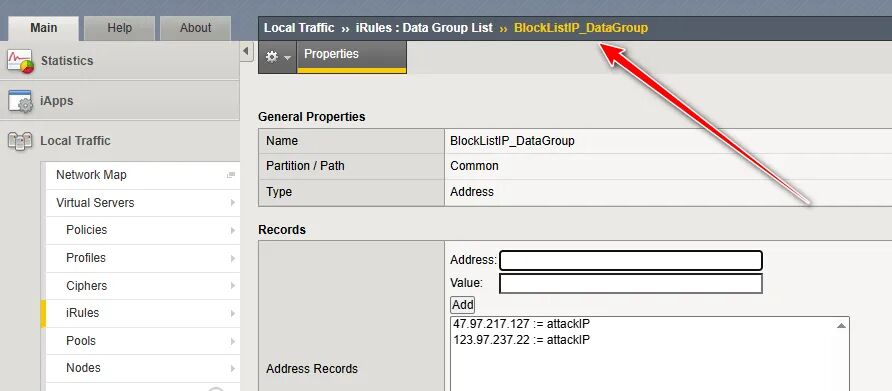
(图片点击放大查看)
2、新建iRules
例如
when FLOW_INIT { if { [class match [IP::remote_addr] equals BlockListIP_DataGroup]} { log local0. "Attacker IP [IP::client_addr]" drop } }
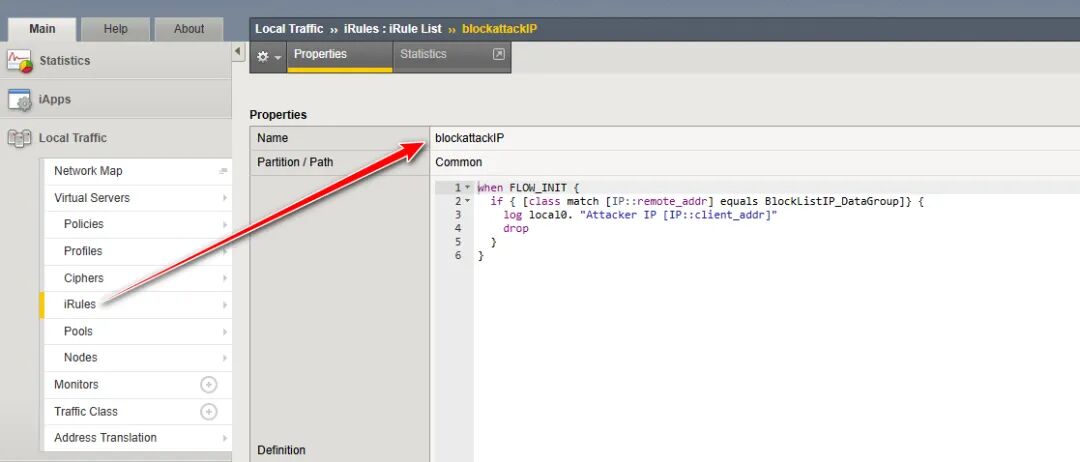
3、在VS的Resoures中应用这个iRules模板即可
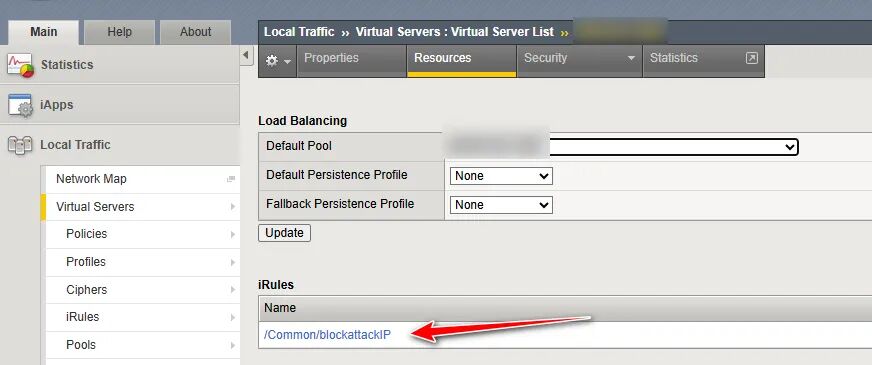
这样就只用在Data Group List添加攻击IP黑名单即可进行拦截
本文参与 腾讯云自媒体同步曝光计划,分享自微信公众号。
原始发表:2025-04-11,如有侵权请联系 cloudcommunity@tencent.com 删除
本文分享自 WalkingCloud 微信公众号,前往查看
如有侵权,请联系 cloudcommunity@tencent.com 删除。
本文参与 腾讯云自媒体同步曝光计划 ,欢迎热爱写作的你一起参与!
评论
登录后参与评论
推荐阅读
目录

